Solutions
By connecting disparate information and big data to close the investigative loop, Point Duty’s solutions enable you to be the first to know and the first to act.
Increased pressure to deliver results in less time – but with reduced resources and budgets.
Creating reports and deriving meaningful, actionable intelligence while grappling with these issues is no easy task.

The key pain points of big data
For every case, analysts receive multiple unstructured and structured pieces of data. It then needs to be processed in a way that extracts key data such as Entities, Links and Properties (ELP) – essential for enabling the investigation to pivot rapidly through the data to conduct visual and geospatial analysis.
Analysts must overcome issues such as:
- Data management
- Storage and retrieval of data stored in different formats and on legacy systems
- Information and intelligence sharing
- Manual processing of documents
- Visualizing and presenting information
Leveraging big data to empower analysts
Streamlining the process means bringing on board a centralised database in which to store, access and analyse data with real time connectivity outwards to frequently accessed data sources.
These could include:
- Internal police sources such as criminal or registration databases
- Information gained through subpoenas such as CCTV or phone records
- Open source intelligence (OSINT)
Customised to meet individual needs and requirements
Point Duty’s Law Enforcement solution packages include the provision of the following key intelligence productivity tools, either individually or in combination:
Threat Hunter ®

Point Duty’s Threat Hunter ® solution-set provides a range of tools and a unique integration of capabilities to dramatically improve data management, enrichment and insights enabling investigations to complete more effectively and in less time.
The solution is both flexible and scalable based on client requirements with custom solutions available for enterprise deployments. Custom deployments can include connection to and integration of client and 3rd party data sources.






- Smoke Detection
- ANPR
- Entity Resolution
- PD Lynx Browser for i2
- PD Esri for i2
- i2 Analyst’s Notebook
- Entity Extraction
Smoke Detection through AI
Point Duty's smoke detection solution is engineered for rapid response and comprehensive monitoring of Camera streams and still images.
- Real Time Smoke Detection: Quickly identifies smoke presence within seconds, enabling prompt action.
- Smart Notifications: Delivers alerts via Email and SMS, customisable to ensure you receive the information you need when it matters most.
- Visual Verification: Provides images along with notifications, highlighting areas affected by smoke with adjustable frames for precise monitoring.
- Configurable Dectections: Offers configuration of detection thresholds, notification intervals, and monitoring times to fit specific site requirements.
- Scalability and Versatility: Easily adapts to different scales of operation, with options for both internal and external hosting.
- Optisions for Enhanced User Interface:
- Track current and past alerts.
- Monitor live streams and receive Smoke Alerts directly.
- Navigate an interactive map to view smoke direction and location
- Reliable System Alerts: Sends notifications about system integrity and performance issues.
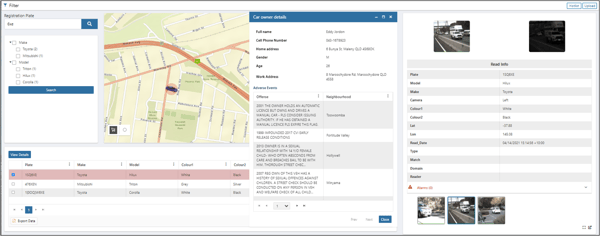
Automatic Number Plate Recognition
Point Duty’s ANPR solution enables AI driven investigations at the enterprise. Detect false or mismatched vehicle plates. Query your data by multiple data points including:
- Number plate
- Partial number plate
- Location
- Owner details*
- Criminal history*
- 900+ vehicle makes
- 300+ models
- 10+ primary colours
*requires connection to internal databases.
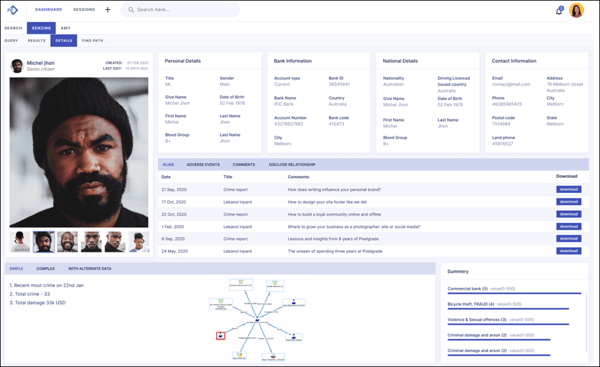
Entity Resolution powered by Senzing
Senzing real-time AI for entity resolution provides federal, state and local government agencies and other public sector organisations with powerful insights about who is who and who is related to who.
- Gain visibility of both obvious and non-obvious relationships between individuals while discovering human error, informational inconsistency and deliberate duplicity.
- Machine Learning (ML) and Artificial Intelligence (AI) models ensure that minimal data preparation is required. Minimal training overheads ensure that capability is immediately realised.
PD Lynx Browser for i2
Conduct web-based research and collection fully integrated within i2 Analyst’s Notebook.
- Conduct OSINT research
- Add web content to the chart as an entity or property
- Open PDFs from within i2 ANB
- Submit information to Chart, iBase or EIA information store
- Archive web page
- Entire page for standard website
- Captures selected area of social media site
- Can be unpinned from i2 ANB and run in a separate screen.
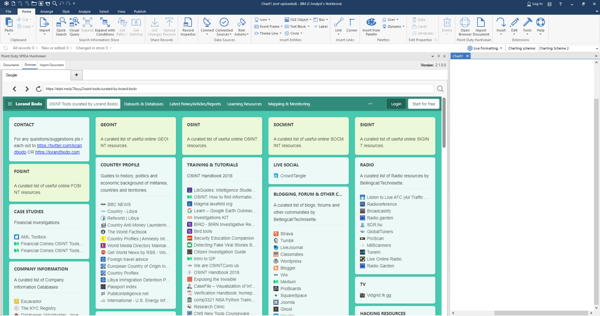
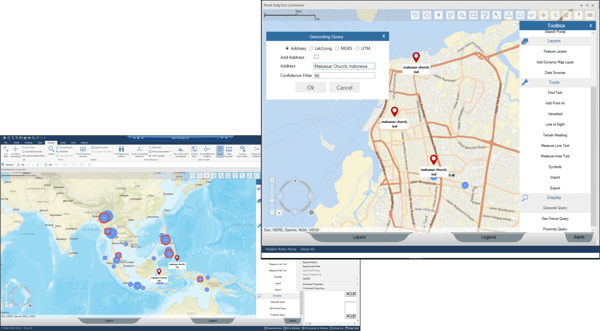
Point Duty Esri Connector for i2 Analyst’s Notebook
Esri are the world’s leading provider of Geospatial Intelligence Solutions (GIS) solutions.
Point Duty has created a connector that links the extensive GIS capabilities of Esri ArcGIS with the power of i2’s visual analysis. This enables the i2-based analyst to leverage key geospatial features to enhance their analysis.
The seamless integration with the i2 Chart enables items to be instantaneously visualised if they have coordinates attached.
- Direct relationship with the chart
- Create shapes
- Create and upload overlays
- Upload and share Geospatial files
- Clustering of events
- Line of site
- Geospatial queries
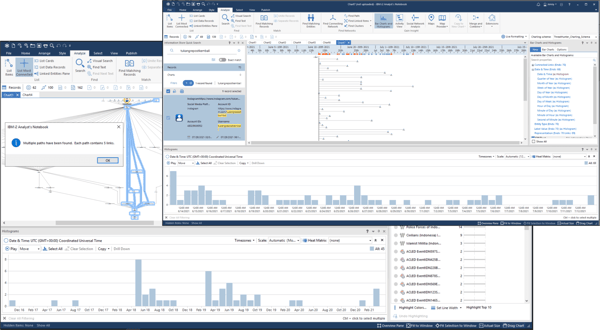
i2 Analyst’s Notebook – the world’s leading visual analytics tool
- Link analysis: Visualise data in association charts to see relationships between entities such as people and organizations and illustrate how they are interconnected.
- Timeline analysis: Go beyond how entities are interconnected by portraying information in a timeline.
- Statistical views: Use bar charts and histograms to look at the distribution of data in your chart and drill down, concentrating on information that is of interest.
- Heat matrices: Can be used to quickly gain insight into your data and identify areas for further analysis.
- Social network analysis: Help your analysts examine and analyse group structures and communication flows within networks. This powerful capability enables users to better understand relationships between entities on their charts.
- Advanced analytics: Use capabilities such as Find Connecting Network to find a network that connects several entities, directly or indirectly, and List Most Connected to identify most active items, greatest number of connections or largest transactions.
Super charge your investigations by generating pivot points within your documents
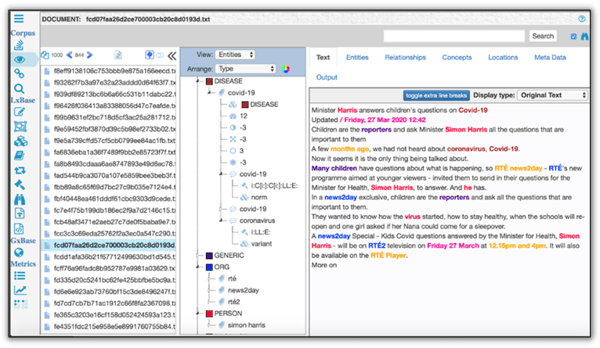
With Entity Extraction, you can identify over 3 dozen entity types, 500+ relationships, and resolve entities across multiple documents. Tiered and scalable solution set enables these capabilities to be leveraged from the individual to enterprise level.
Automate the identification and tagging of all-important entities, and the links between entities, in unstructured documents for the analyst. The entities, links and documents are available in i2 for vetting, analysis, and the building of meaningful charts to better support the mission.
- Process documents in over 200 languages
- Extract Entities, Links and Properties
- Integrates seamlessly with i2 products
- Geospatial extraction generates coordinates from documents
- Sentiment analysis